Fraudulent domains masquerading as Microsoft’s Home windows 11 obtain portal are trying to trick customers into deploying trojanized set up information to contaminate programs with the Vidar info stealer malware.
“The spoofed websites have been created to distribute malicious ISO information which result in a Vidar info-stealer an infection on the endpoint,” Zscaler stated in a report. “These variants of Vidar malware fetch the C2 configuration from attacker-controlled social media channels hosted on Telegram and Mastodon community.”
Among the rogue distribution vector domains, which have been registered final month on April 20, include ms-win11[.]com, win11-serv[.]com, and win11install[.]com, and ms-teams-app[.]internet.
As well as, the cybersecurity agency cautioned that the risk actor behind the impersonation marketing campaign can be leveraging backdoored variations of Adobe Photoshop and different official software program akin to Microsoft Groups to ship Vidar malware.
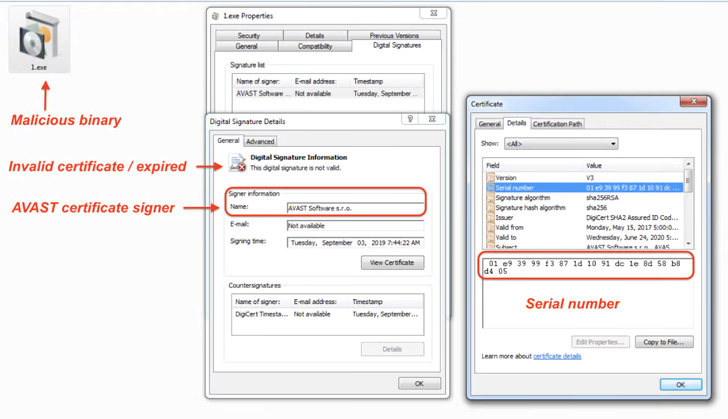
The ISO file, for its half, incorporates an executable that is unusually massive in dimension (over 300MB) in an try to evade detection by safety options and is signed with an expired certificates from Avast that was doubtless stolen following the latter’s breach in October 2019.
However embedded throughout the 330MB binary is a 3.3MB-sized executable that is the Vidar malware, with the remainder of the file content material padded with 0x10 bytes to artificially inflate the scale.
Within the subsequent section of the assault chain, Vidar establishes connections to a distant command-and-control (C2) server to retrieve official DLL information akin to sqlite3.dll and vcruntime140.dll to siphon worthwhile information from compromised programs.
Additionally notable is the abuse of Mastodon and Telegram by the risk actor to retailer the C2 IP tackle within the description discipline of the attacker-controlled accounts and communities.
The findings add to an inventory of various strategies which have been uncovered previously month to distribute the Vidar malware, together with Microsoft Compiled HTML Assist (CHM) information and a loader known as Colibri.
“The risk actors distributing Vidar malware have demonstrated their means to social engineer victims into putting in Vidar stealer utilizing themes associated to the most recent fashionable software program purposes,” the researchers stated.
“As all the time, customers must be cautious when downloading software program purposes from the Web and obtain software program solely from the official vendor web sites.”